HIPAA Compliance in 2026: OCR Has Raised the Bar—Here’s What SMB Healthcare Must Do Now
If you sit in a compliance seat, you already know the uncomfortable truth: HIPAA is no longer being enforced like a “policy and training” regime. HHS...
4 min read
![]() Palindrome Technologies
:
Jun 18, 2025 8:37:00 AM
Palindrome Technologies
:
Jun 18, 2025 8:37:00 AM
The landscape of healthcare data privacy is undergoing a significant transformation in 2025, with federal regulators rolling out some of the most substantial updates to the Health Insurance Portability and Accountability Act (HIPAA) in recent years. Driven by the escalating threat of cyberattacks and a shifting legal environment, these new rules demand a proactive and robust compliance strategy from all healthcare organizations and their business associates. For companies navigating this new terrain, a "business as usual" approach to HIPAA is no longer a viable option.
This article breaks down the crucial updates to HIPAA rules and provides actionable recommendations to help your healthcare organization stay ahead of the curve and proactively protect patient data.
This year's updates touch upon both the Privacy and Security Rules, with a heavy emphasis on fortifying defenses against digital threats and enhancing patient rights.

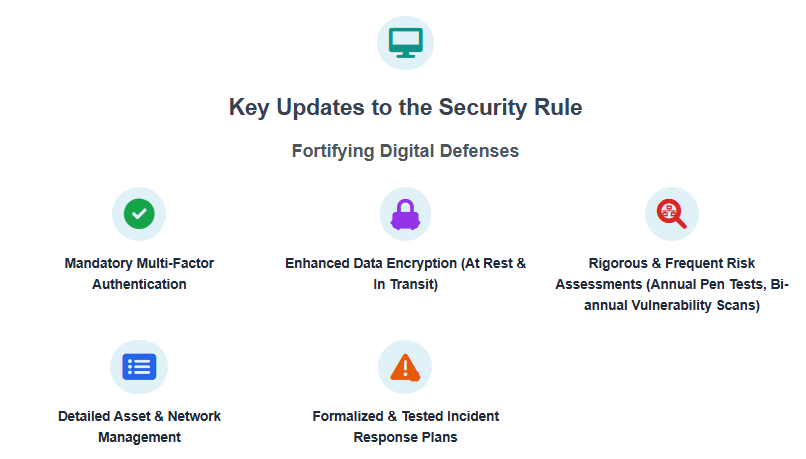
Sweeping Changes to the Security Rule:
The most significant changes are concentrated in the HIPAA Security Rule, reflecting a direct response to the alarming increase in data breaches and ransomware attacks targeting the healthcare sector. Key mandates and stricter requirements include:
Evolving Privacy Rule and Patient Rights:
The HIPAA Privacy Rule has also seen important updates, primarily focused on empowering patients and safeguarding sensitive information:

In this heightened regulatory environment, a proactive, rather than reactive, approach to HIPAA compliance is essential. Here are key recommendations for healthcare companies:
1. Conduct a Comprehensive and Continuous Risk Analysis: This is the cornerstone of a strong HIPAA security program. Go beyond a simple checklist. Your risk analysis should be a thorough, ongoing process that identifies potential threats and vulnerabilities across your entire organization, including all systems that store or transmit ePHI. Engage a third-party cybersecurity firm to conduct penetration testing and vulnerability assessments to get an unbiased view of your security posture.
2. Modernize Your Security Infrastructure: Invest in and implement the necessary technologies to meet the new security mandates. This includes:
3. Develop and Test a Robust Incident Response Plan: Don't wait for a breach to happen. Develop a detailed incident response plan that outlines the steps to be taken in the event of a security incident. This plan should be regularly tested through tabletop exercises to ensure all team members know their roles and responsibilities.
4. Prioritize Employee Training and Awareness: Your employees are your first line of defense. Conduct regular, engaging, and role-specific HIPAA training. This should include education on identifying phishing attempts, the importance of strong passwords, and the proper handling of PHI. Document all training activities.
5. Strengthen Business Associate Agreements and Vendor Management: The security failures of your vendors can become your compliance nightmare. Review and update all Business Associate Agreements (BAAs) to ensure they reflect the latest HIPAA requirements. Conduct due diligence on all vendors who have access to your patients' PHI to verify their security practices.
6. Foster a Culture of Compliance: HIPAA compliance should not be solely the responsibility of the IT department or a compliance officer. It must be ingrained in the culture of your organization. Leadership must champion the importance of patient privacy and data security, and this message should be consistently communicated to all staff.
The latest HIPAA rules represent a new era of accountability for the healthcare industry. By embracing these changes and taking a proactive approach to compliance, healthcare organizations can not only avoid costly penalties but also build trust with their patients by demonstrating a steadfast commitment to protecting their most sensitive information.

By focusing on a threat-adoptive and research-based approach, Palindrome Technologies delivers a multi-layered security strategy tailored to the unique challenges of the healthcare sector. Their core offerings directly address the key vulnerabilities and regulatory requirements highlighted in the latest HIPAA updates:
HIPAA & HITRUST® Focused Risk Management: Palindrome Technologies moves beyond generic checklists, offering in-depth HIPAA Risk Assessments that provide a thorough analysis of potential risks to electronic Protected Health Information (ePHI). As a Certified HITRUST CSF External Assessor, they possess the expertise to guide organizations through the complexities of HITRUST certification, a framework that harmonizes HIPAA with other rigorous standards to demonstrate the highest levels of assurance.
Medical Device & IoT Security: A key area of specialization is the security of connected medical devices (IoMT). Palindrome Technologies is an officially recognized testing facility for the IEEE Medical Device Cybersecurity Certification Program and provides services to help manufacturers prepare for FDA 510k pre-market submissions. Their device security testing and assurance capabilities help identify and remediate vulnerabilities throughout the product lifecycle, from development to deployment.
Offensive Security and Infrastructure Defense: To proactively identify weaknesses before they are exploited, the firm conducts adversarial testing, including penetration testing of internal and external networks, web applications, and cloud environments. Their services extend to in-depth Open Source Intelligence (OSINT) gathering to uncover an organization's internet footprint and potential data leakage.
Governance, Risk, and Compliance (GRC): Palindrome Technologies assists healthcare organizations in developing and implementing effective risk management frameworks that align with multiple regulatory standards. This strategic approach helps to avoid costly penalties, enhance reputation, and ensure that security investments are aligned with business objectives.
By engaging a specialized and accredited partner such as Palindrome Technologies, healthcare organizations can access the deep technical expertise and strategic guidance needed to build a resilient and compliant security program. This allows them to focus on their primary mission of delivering exceptional patient care, confident that their sensitive data and critical systems are protected by a proactive and expert defense.
If you sit in a compliance seat, you already know the uncomfortable truth: HIPAA is no longer being enforced like a “policy and training” regime. HHS...
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a cornerstone of patient data protection in the United States. At its...
The Health Insurance Portability and Accountability Act (HIPAA) is more than just a set of rules; it's the bedrock of patient trust in the digital...
3 min read
In today's interconnected healthcare landscape, the cybersecurity of medical devices is paramount. As medical technology becomes more...