The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a cornerstone of patient data protection in the United States. At its heart, HIPAA aims to safeguard Protected Health Information (PHI) – any individually identifiable health information – by setting national standards for its privacy and security. Healthcare companies, including providers, health plans, and healthcare clearinghouses, along with their business associates who handle PHI on their behalf, are mandated by the government to implement and maintain robust administrative, physical, and technical safeguards.
These requirements, primarily outlined in the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule, dictate how PHI can be used, disclosed, stored, and transmitted. The goal is clear: ensure the confidentiality, integrity, and availability of patient information, thereby fostering patient trust and enabling the secure use of health data for crucial healthcare operations.
However, achieving and maintaining HIPAA compliance is an ongoing journey, fraught with complexities. Organizations often grapple with several core challenges:
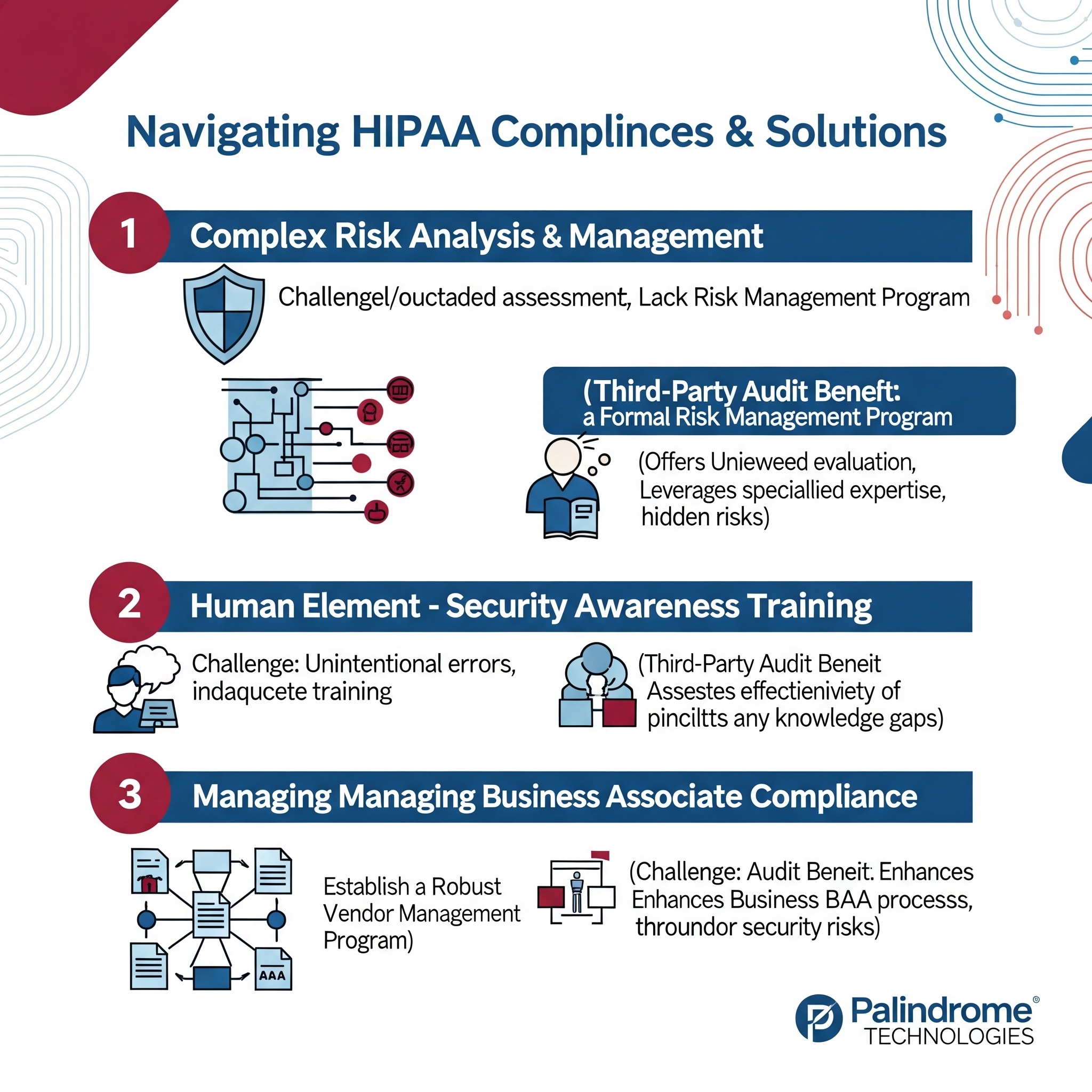
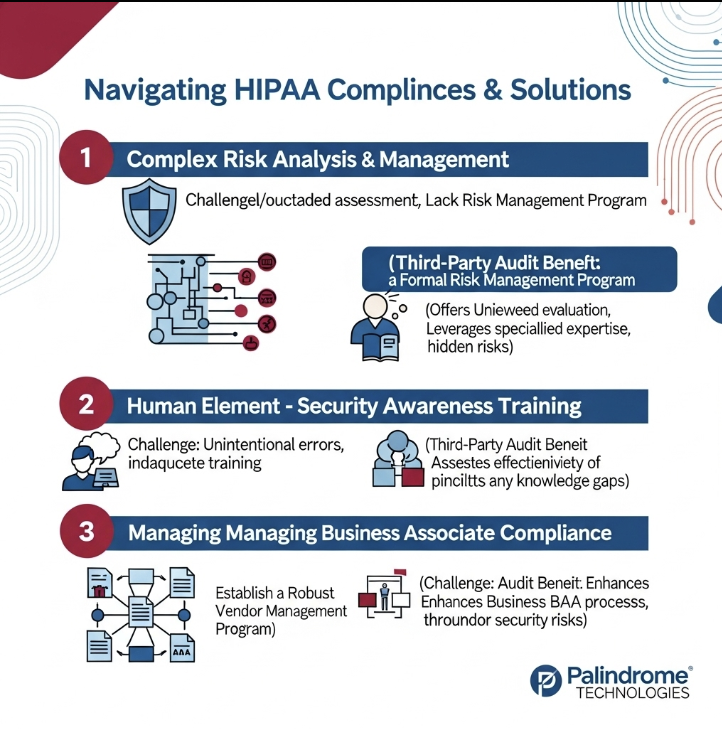
3 Core HIPAA Compliance Challenges
-
The Labyrinth of Risk Analysis & Management:
- Challenge: HIPAA mandates regular and thorough risk analyses to identify potential threats and vulnerabilities to PHI. Many organizations struggle with the scope and depth required, performing superficial assessments, failing to update them in response to environmental or operational changes, or lacking the expertise to truly understand and prioritize identified risks. This can leave significant gaps in their security posture.
- Addressing the Challenge: A foundational step is to establish a formal risk management program. This involves not just identifying assets and threats, but also evaluating the likelihood and impact of those threats and implementing reasonable and appropriate security measures to mitigate them. While internal assessments are a starting point, a third-party HIPAA audit brings invaluable objectivity and specialized expertise. External auditors are unhindered by internal biases or familiarity that might overlook vulnerabilities. They often possess a broader understanding of current threat landscapes and regulatory interpretations, utilizing advanced tools and methodologies to conduct a more comprehensive assessment. This independent validation can uncover hidden risks and provide a clearer, actionable roadmap for remediation, far exceeding what many in-house teams or automated checklists can achieve on their own.
-
The Human Element: Ensuring Robust Employee Training & Awareness:
- Challenge: Employees are often the first line of defense, but also a common source of breaches – frequently unintentional. Inadequate or infrequent training, a lack of understanding of specific policies and procedures, or a failure to instill a culture of security can lead to careless handling of PHI, falling victim to phishing scams, or improper disclosures.
- Addressing the Challenge: Implementing a continuous security awareness training program is crucial. This should cover HIPAA basics, organizational policies, recognizing and reporting potential threats, and role-specific responsibilities regarding PHI. Training should be engaging, regularly updated, and reinforced. A third-party auditor doesn't just check if training occurred; they can assess its effectiveness. They can review training materials for comprehensiveness and relevance, evaluate employee understanding through various methods, and identify areas where current training programs are falling short. This expert review helps organizations tailor their training to address specific weaknesses and ensure it genuinely prepares employees to protect PHI.
-
The Extended Web: Managing Business Associate Compliance:
- Challenge: Healthcare organizations increasingly rely on third-party vendors (Business Associates) for various services, many of whom handle PHI. Ensuring that every Business Associate has a compliant Business Associate Agreement (BAA) in place, and more importantly, that they themselves are adhering to HIPAA standards, is a significant undertaking. A breach caused by a vendor can still result in severe penalties and reputational damage for the covered entity.
- Addressing the Challenge: Robust vendor management programs are essential. This includes due diligence before engaging a vendor, ensuring comprehensive BAAs are executed, and periodically assessing the security practices of Business Associates. Third-party auditors can play a critical role in strengthening Business Associate management. They can help organizations develop standardized BAA templates and review existing agreements for adequacy. Furthermore, an independent audit can extend to assessing the organization's processes for vendor risk assessment and ongoing monitoring. This provides assurance that the entire ecosystem handling PHI is held to the required security standards.
The Palindrome Technologies Advantage
Beyond avoiding severe financial penalties (which can run into millions of dollars) and the significant reputational damage a breach can cause, proactive HIPAA compliance builds patient trust and enhances operational resilience. Patients are more likely to engage with and trust healthcare organizations that demonstrate a strong commitment to protecting their sensitive information.
This is where partnering with a specialized cybersecurity and compliance firm like Palindrome Technologies offers distinct incentives and benefits.
Palindrome Technologies brings a wealth of experience, dating back to 1995, in securing complex environments for both commercial and government organizations. They understand that true HIPAA compliance goes beyond tick-box exercises. Their approach emphasizes:
- Expert-Driven HIPAA Risk Assessments: Palindrome Technologies conducts thorough assessments of potential risks, threats, and vulnerabilities specific to your environment. They don't just rely on automated tools; they focus on validating the effectiveness of your implemented security measures.
- Comprehensive Security Testing: Their services often include crucial elements such as internal and external penetration testing, physical security analysis, and Open Source Intelligence (OSINT) analysis to identify data leakage or misconfigurations.
- Incident Response Readiness: They can evaluate the effectiveness of your incident response plan through adversarial scenario emulations, ensuring you are prepared to act decisively should a breach occur.
- Guidance Towards Higher Assurance: Palindrome Technologies helps clients not only meet regulatory requirements but also demonstrate the highest levels of assurance to stakeholders. They have experience guiding organizations through certifications like HITRUST CSF, which has a strong mapping to HIPAA.
- Deep Industry Involvement: Their participation in key industry initiatives and contributions to cybersecurity standards (including FCC CTM, NIST, ISACA, IEEE) means they are at the forefront of evolving security best practices.
By working with Palindrome Technologies, healthcare organizations gain an impartial, expert partner dedicated to identifying and mitigating risks effectively. This collaboration provides a clear path to a robust security posture, ensuring that patient data is protected, regulatory mandates are met, and the organization can focus on its core mission of providing excellent patient care with confidence. Investing in such expertise is investing in the security, integrity, and future of your healthcare operations.
![]() Palindrome Technologies
:
May 26, 2025 10:34:30 AM
Palindrome Technologies
:
May 26, 2025 10:34:30 AM