Private 5G Security
Evaluate the security of your private 5G implementation through rigorous testing
Build your private 5G with security and resilience
The fifth generation (5G) telecommunication system aims to deliver enhanced mobile broadband, massive machine type communications, and ultra-reliable and low latency communications to consumers and enterprise organizations.
The 5G security architecture leverages the 4G security mechanisms but also introduces new features and service components to provide greater scalability and security in support of emerging technologies. Some of the notable new features include:
- Service based Architecture (SBA)
- Network Slicing and Multi-tenancy
- Control Plane User Plane separation
- Unified Non-3GPP Network Access
Although, 5G introduces unique functions to support the evolution of next generation services it also relies on several cloud computing technologies including software defined networking (SDN), network function virtualization (NFV), virtualization and multi-access edge computing (MEC).
Furthermore, the 5G ecosystem leverages several standards and protocols (e.g., NAS, DIAMETER, SIP, HTTP2/TLS) to support a variety of use-cases for both consumers and enterprise organizations (e.g., Industry 4.0/M2M, Telemedicine, AV/VR, smart-cities).
This amalgamation of complex technologies, and the multitude of interactions and interdependencies between the various architectural elements (e.g., radio-access, core network-elements, network functions and protocols) increase the level of complexity and consequently introduce new attack vectors.
Our penetration testing service focuses on evaluating the security posture of your private 5G network end-to-end and provide the following benefits:
- Identify critical vulnerabilities that can be used by adversaries to impact your operations
- Determine the viability of applicable attacks (real-world scenarios)
- Measure the risk and impact of the corresponding threats
- Provide recommendations of improvement
- Enhance your security posture and network reliability
Evaluating the Security of your private 5G
To evaluate the external and internal security posture of a private 5G implementation, we use a multi-dimensional security assessment approach derived from research and our prior experience conducting security analysis of carrier-grade and enterprise 5G networks.
The areas of evaluation include (but not limited to):
- Signaling and bearer traffic security analysis; end-to-end call flow analysis of signaling and user plane controls (e.g., NAS authentication, confidentiality, impersonation/Rogue gNB)
- Network Interfaces security; Network Functions and protocols analysis (e.g., NAS, HTTP2, DIAMETER)
- Network Element security configuration; bare-metal and/or virtualization/cloud (i.e., Kubernetes, pods) security analysis
- Management interfaces (OAM&P) security analysis (e.g., input validation, path-traversal, role-based access, privilege escalation)
- Hardware security analysis of the gNB and/or other Radio Access nodes (e.g., eFemto)
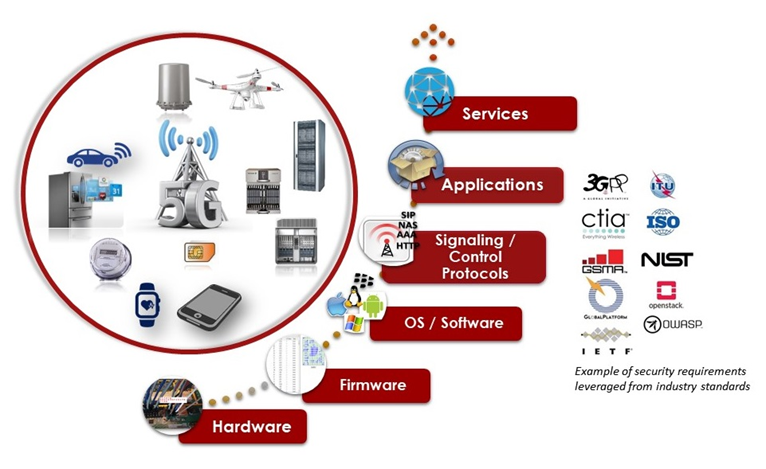
Private 5G Security Testing
Palindrome’s security assurance testing methodology leverages techniques and methods that focus on validating the target component’s security along with end-to-end service flows to determine proper alignment with industry standards and best security practices. The figure above provides a conceptualization of the various layers that are addressed by the methodology, including, platform software, signaling protocols, control plane protocols, administration, management and provisioning, applications and services and device hardware (i.e., JTAG, eMMC, tamper resistance controls) as applicable to the scope.
Why Choose Palindrome Technologies?
Our team has been on the forefront of Cyber security since 1995 and supporting commercial and government organizations with securing high-assurance environments and emerging technologies. In addition to our extensive experience we participate in key industry initiatives to provide thought leadership and contributions to help improve Cyber security standards and frameworks, including FCC, NIST, IEEE, GSMA, CTIA, and ISA standards.
Start Securing Your private 5G
Leaving your mission-critical systems vulnerable can impact your operations, impact client services and damage your reputation.
Palindrome Technologies can help you demonstrate the highest levels of assurance to stakeholders and your commitment to keep your customers secure along with aligning with regulatory guidance for critical infrastructure.

