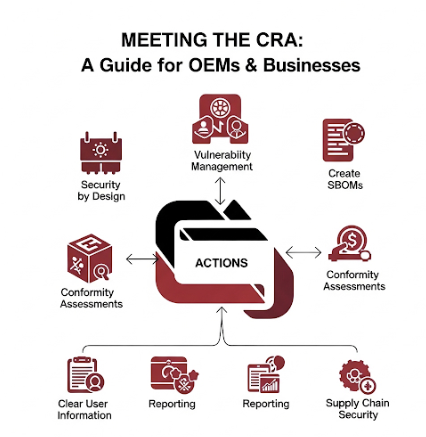
Texas Legislation (SB 2610)- Cybersecurity Safe Harbor for Small Businesses - What you need to know and steps to prepare
The digital landscape presents an ever-evolving challenge for businesses of all sizes, but none are more acutely vulnerable than small and...