U.S. Cyber Trust Mark IoT Device Security Certification
Demonstrate your commitment to Cyber Resilience through CTM device certification.
Palindrome Technologies acts as both a Cybersecurity Labeling Administrator (CLA) and an accredited CyberLab within the US Cyber Trust Mark (US CTM) Certification Scheme. We are dedicated to helping manufacturers achieve compliance for their IoT devices, enhancing the resiliency of the US cyber infrastructure, and protecting consumers by ensuring devices meet recognized cybersecurity best practices.
Our Role as a Cybersecurity Labeling Administrator (CLA)
As a CLA, Palindrome Technologies plays a crucial role in overseeing the security evaluation and certification process for IoT products. Our responsibilities include:
- Reviewing Evaluation Reports and Making Certification Decisions: We review reports submitted by CyberLabs and make final certification decisions, ensuring IoT products comply with US CTM requirements before issuing certification.
- Conducting Post-Market Surveillance: We perform post-market surveillance, which includes random testing and compliance verification of certified products.
- Managing Certificate Actions: We manage certificate suspensions or revocations if products fail to maintain compliance.
- Participation in Governance: We actively participate in the US CTM Governance Committee to maintain and interpret certification requirements.
- Handling Public Complaints: We receive and handle public complaints related to the misuse of the Cyber Trust Mark.
- Maintaining Records: We maintain records of certified IoT products and ensure compliance with certification policies.
- Collaboration on Scheme Updates: We collaborate with the Lead Administrator and Governance Committee on scheme updates and requirement clarifications.
Our Role as an Accredited CyberLab
Palindrome Technologies, as an independent testing laboratory, is accredited under ISO/IEC 17025 and recognized for conducting security evaluations of IoT products under the US CTM scheme. Our responsibilities as a CyberLab include:
- Performing Security Evaluations: We conduct functional security evaluations of IoT products.
- Preparing Evaluation Reports: We prepare comprehensive evaluation reports with testing results and security recommendations for CLAs.
- Ensuring Testing Consistency: We ensure testing consistency through intercomparison exercises.
- Providing Technical Justifications: We provide technical justifications when attestation is used instead of direct testing.
- Reviewing Security-Relevant Changes: We review security-relevant changes to IoT products to determine whether additional testing is needed.
Obtaining the U.S. Cyber Trust Mark through Palindrome Technologies offers several advantages:
- Market differentiation and consumer trust
- Enhanced product security and risk mitigation
- Comprehensive security evaluations to address critical data and system vulnerabilities
IoT device managers that prioritize U.S. Cyber Trust Mark certification can capitalize on first-mover advantages, maximize customer trust while enhancing product security.
To be eligible for the U.S. Cyber Trust Mark, products must:
- Meet FCC's cybersecurity standards
- Obtain authorization to use the Cyber Trust Mark from an appointed CLA
- Undergo testing by an accredited and FCC-recognized Testing Lab, such as Palindrome.
The certification process involves two main steps:
-
Certification Application: After testing, manufacturers submit an application with supporting documents to a Cybersecurity Label Administrator such as Palindrome Technologies.
- Product Testing: Manufacturers must use an accredited Cybersecurity Testing Lab (CyberLab) to verify compliance with FCC's U.S. Cyber Trust Mark guidelines.
Palindrome Technologies streamlines this process by offering:
- Assistance with preparation for certification
- Guidance throughout the certification process
- Testing and certification of IoT products
- Post market surveillance
Palindrome provides manufacturers with streamlined application review and management for FCC IoT Label usage authorization, assistance with preparation for certification, and guidance throughout the certification process. The U.S. Cyber Trust Mark program includes the development of a national registry of certified products. This registry will be accessible via a QR code on the product label, providing consumers with easy-to-understand details about each certified device's security features, including:
- Support period for the product
- Information on software patches and security updates
- Steps to configure the device securely
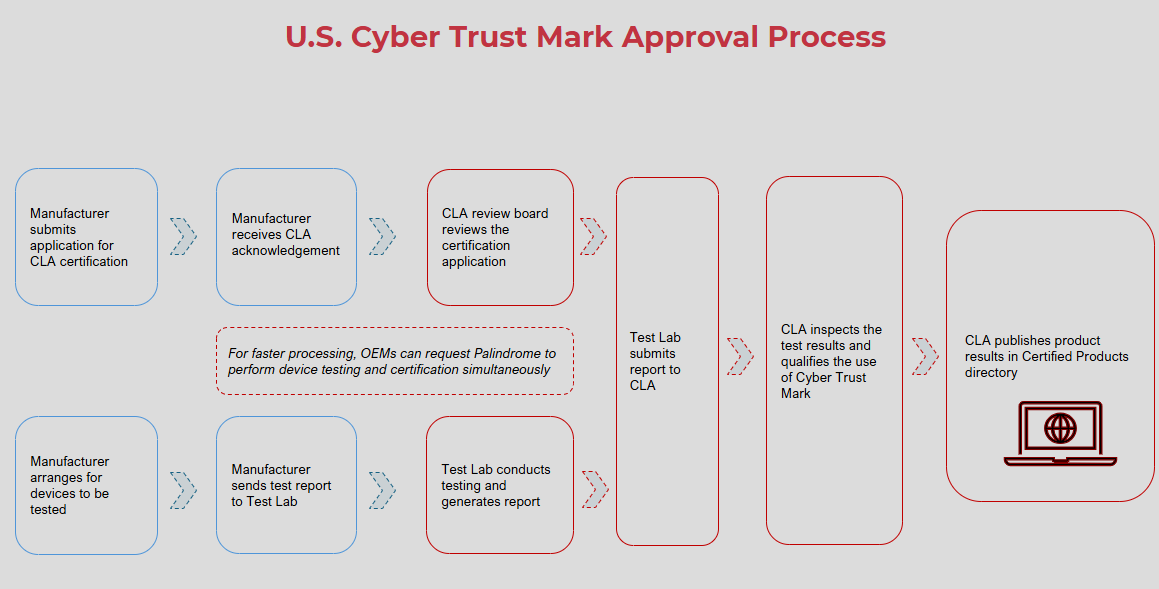
The US CTM Certification Process
The US CTM Certification Scheme follows a structured evaluation process to ensure IoT products meet the required security standards. This process, facilitated by Palindrome Technologies, involves several phases:
1. Preparation Phase
Before formal submission, the applicant (IoT supplier or manufacturer) must prepare all necessary documentation and evidence. This involves:
- Reviewing US CTM security requirements to confirm eligibility.
- Gathering technical documentation, security design artifacts, and implementation details.
- Compiling evidence of security controls, risk assessments, and compliance.
- Deciding whether to contact a CLA directly or engage a CyberLab independently.
2. Application Phase
The formal certification process begins with the submission of an application. Applicants can either:
- Contact a CLA directly: The CLA reviews the request and directs the applicant to select a recognized CyberLab. Alternatively, the applicant may choose one of the approved labs as well.
- Select a CyberLab: The CyberLab then submits an initial certification request to the CLA on behalf of the applicant.
The Application Package includes a description of the IoT product, a list of existing certifications that can serve as evidence, and a justification if multiple product variants are included under the same request. The CyberLab reviews the completeness and accuracy of the package, assesses existing certifications, and determines if a product family approach is applicable.
3. Evaluation Phase
During this phase, our CyberLab conducts security assessments following an approved test plan, which includes functional security verification, vulnerability assessments, and compliance checks.
- Remediation: If minor non-conformities are identified, the applicant must remediate them within a defined timeframe and provide evidence of corrective actions.
- Additional Testing: If the evaluation report is inconclusive, additional testing, retesting, or clarifications may be required.
4. Certification Phase
Upon completion of the evaluation, the CyberLab submits an Evaluation Report and a certification recommendation to the CLA (Palindrome Technologies). The CLA then conducts a thorough review to verify:
- Conformance to US CTM Security Requirements.
- Validity and completeness of testing.
- The CyberLab's recommendation.
- Resolution of any non-conformities.
- Evaluation of any waiver requests.
- Consideration of existing certifications or product families.
Based on this review, a certification decision is made:
- Certification Granted: The IoT product fully complies with US CTM security requirements. A Certificate of Compliance is issued, and the product is added to the public registry.
- Certification Denied: The IoT product fails to meet US CTM security requirements due to major vulnerabilities, non-conformities, or insufficient evidence. The applicant may submit a new application after addressing deficiencies or initiate a dispute resolution process.
Dispute and Interpretation Processes
Palindrome Technologies participates in the established processes for interpretations and disputes to ensure consistency and fairness within the US CTM scheme.
Interpretation Process
This process ensures consistent application of US CTM security requirements and evaluation criteria. Interpretation requests can be initiated by CyberLabs, CLAs, the Lead Administrator, or the FCC. Interpretations can take the form of clarifications, extensions, exemptions, or modifications and policy updates.
Dispute Process
The dispute process provides a structured mechanism for challenging decisions related to certification outcomes, interpretation rulings, and compliance assessments. Disputes can arise from:
- Certification Decision Disputes: When an applicant disagrees with a certification denial or conditional approval.
- Evaluation Process Concerns: When a CyberLab disputes a CLA's request for additional testing or a monitoring requirement.
- Interpretation Disputes: When a CyberLab or CLA challenges an interpretation decision.
- Market Feedback on Certified Products: When concerns are raised regarding the security of a certified IoT product based on vulnerabilities or real-world incidents.
Disputes are formally submitted to the appropriate authority, with escalation paths to the Lead Administrator and the US CTM Governance Committee for resolution.
Certificate Validity and Renewal
US CTM certificates are valid for five years, with annual surveillance evaluations conducted to ensure ongoing security compliance. Special evaluations may also be conducted in response to change management, security incidents, or regulatory concerns.
Documentation Retention
Palindrome Technologies adheres to clear retention policies for all documentation generated during evaluations, surveillance, and certification decision-making. All records related to a certification are retained for five years after the certificate expires or is revoked.
Benefits of Partnering with Palindrome Technologies
By partnering with Palindrome Technologies for US CTM certification, manufacturers can:
- Demonstrate Compliance: Obtain an industry-recognized certification to demonstrate compliance with cybersecurity best practices.
- Improve Market Competitiveness: Enhance market competitiveness and build consumer trust through certified security.
- Ensure Security Transparency: Contribute to enhanced security transparency across the IoT ecosystem, allowing consumers to make informed purchasing decisions.

